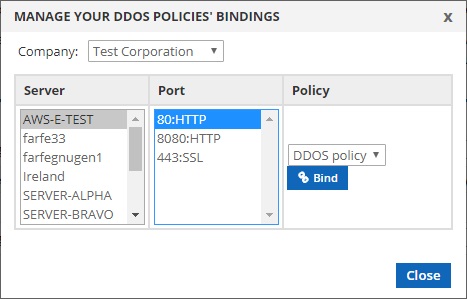
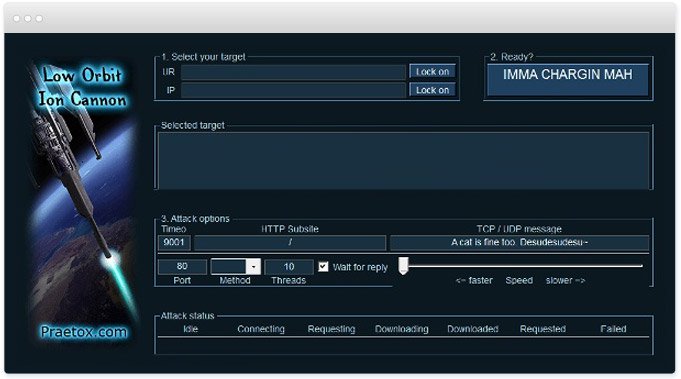
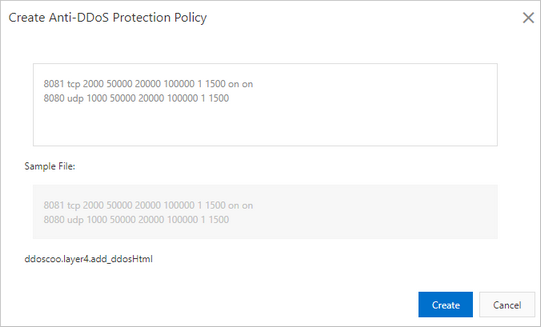
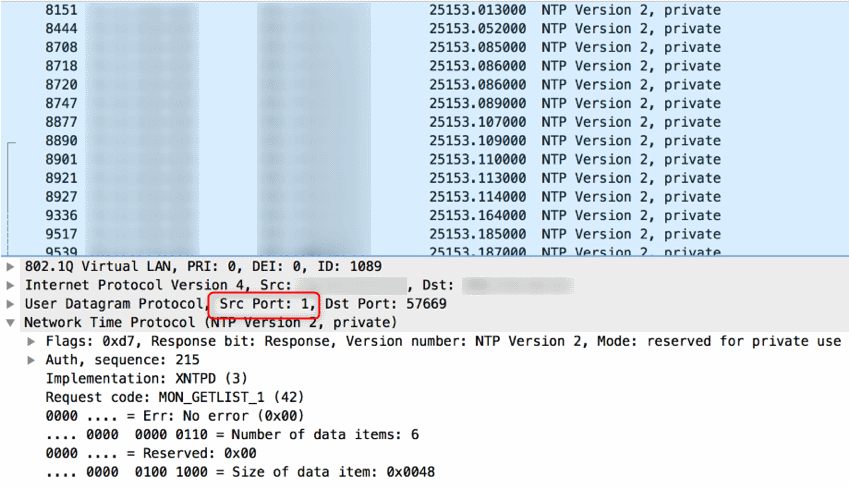
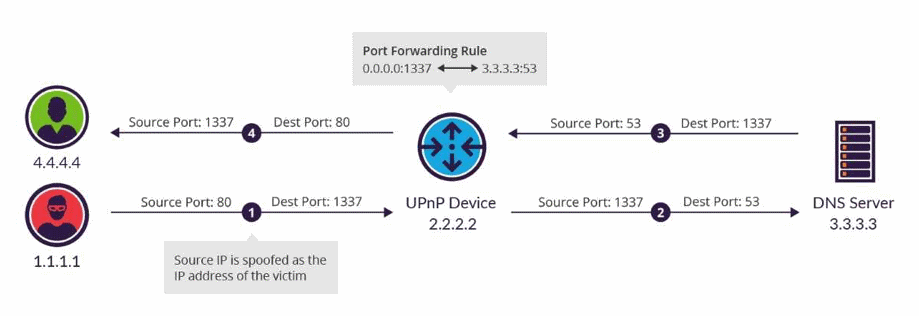
GitHub - T34mV18rs/V-DdoS: A Ddos Attacking Tool By T34m V18r For Termux.. Just Need Website IP To Start Attack & Use The Port Number 8080
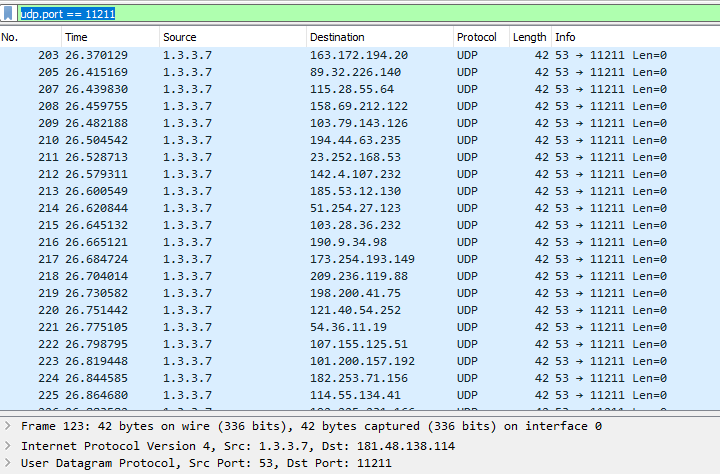
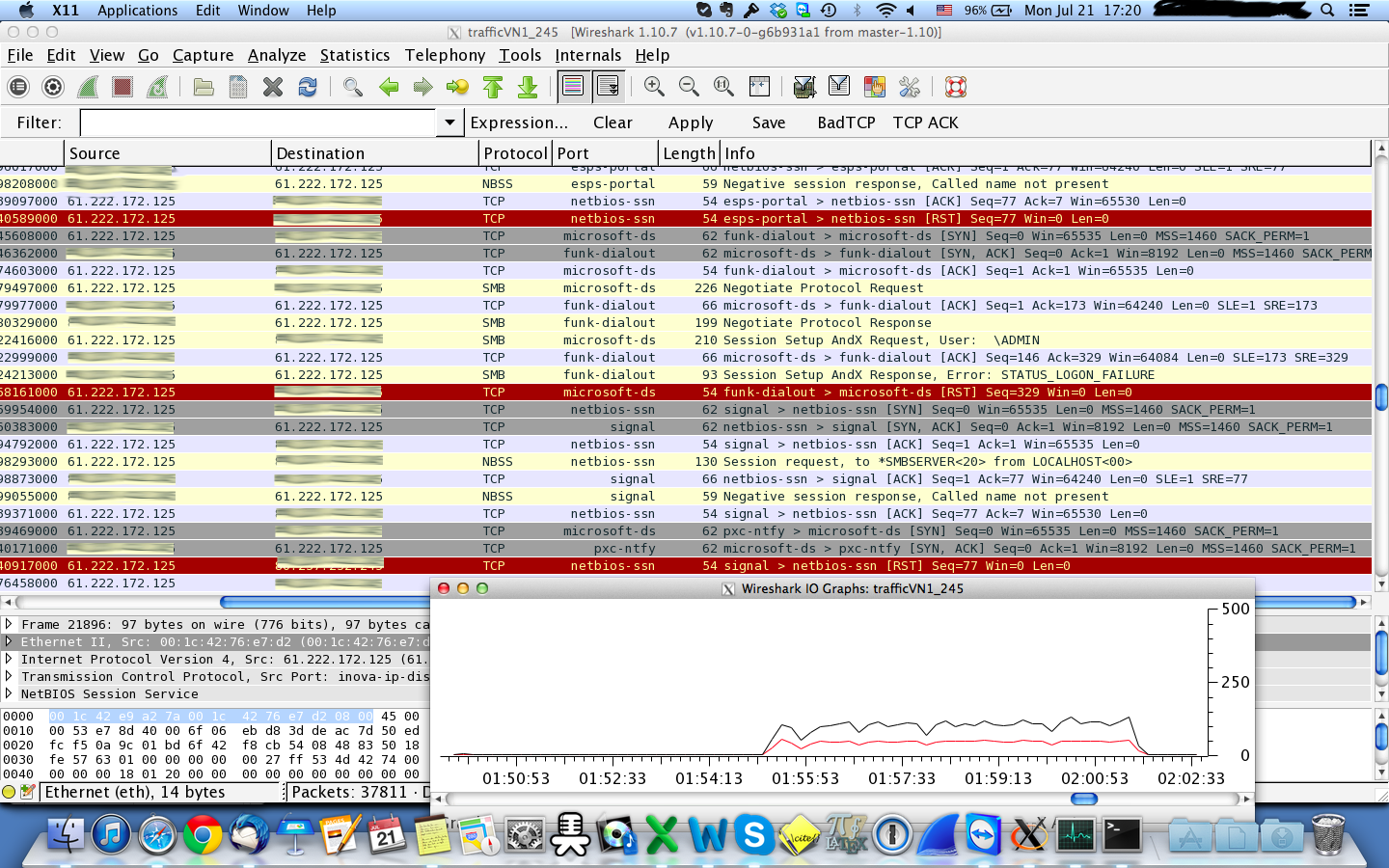
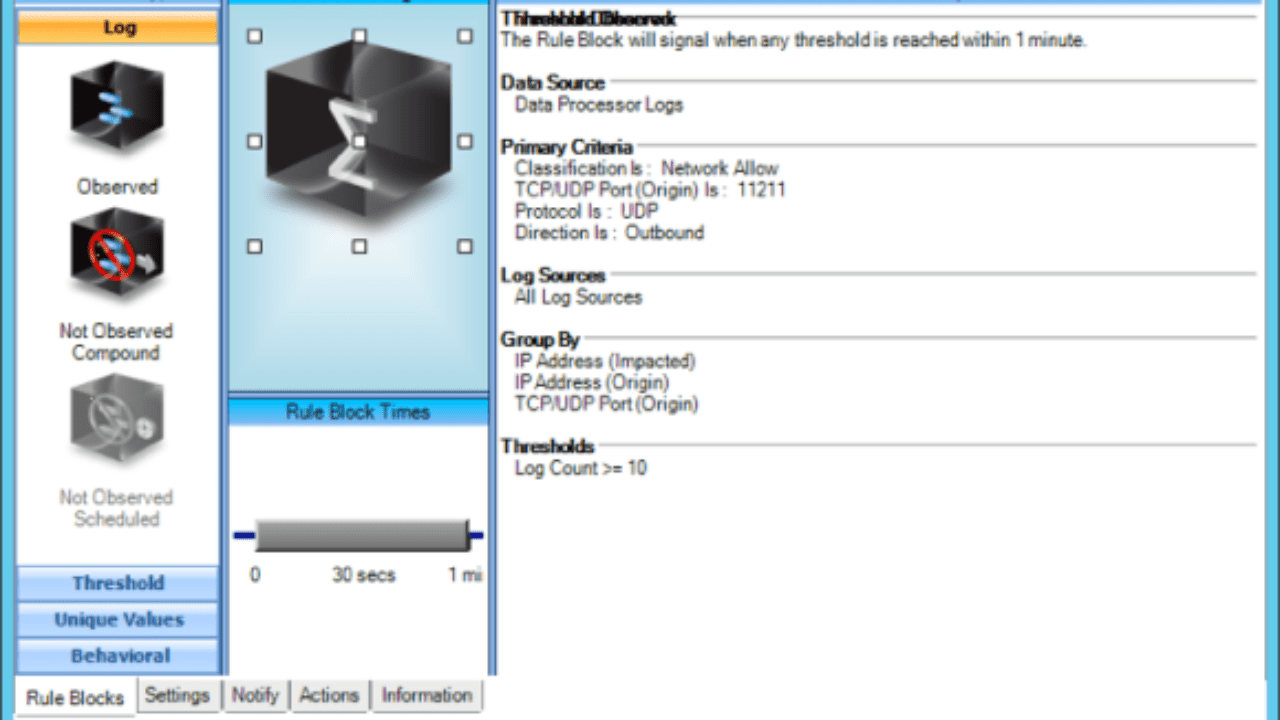
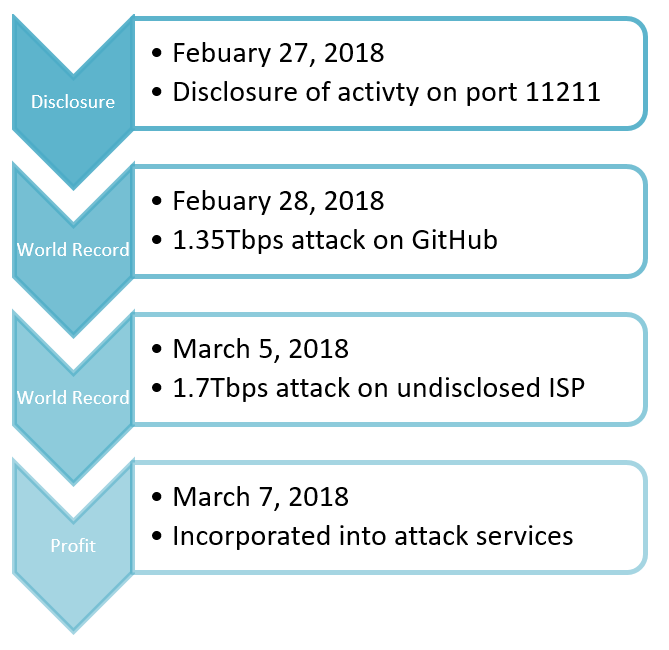
GitHub - 649/Memcrashed-DDoS-Exploit: DDoS attack tool for sending forged UDP packets to vulnerable Memcached servers obtained using Shodan API